FortiGuard
Some tips about troubleshooting of FortiGuard Services.
FORTINET
3/30/20244 min read


When you think about security protection in Fortinet universe, the FortiGuard is the core of many services like Web Filtering, IPS, Application Control, Email Filtering, Industrial DB or Anti Virus and others.
The FortiGuard also known as FortiGuard Distribution Network (FDN) , that is a large group of servers working around the globe to provides updates to antivirus, antispam, and IPS definitions to your FortiGate like it said above. An important point here is the FortiGuard works with subscription services to make possible and provide the updated security solutions to allow the administrator to create and enable security profiles for protections like IPS or Web Filter and even others.
The mains goal here will be understanding how it works and a little troubleshooting for Web Filtering. That service is more sensitive to problems with Internet Service Providers than others because the classification occurs in real time. The others use a local and updatable signature database.
FortiGuard Default Settings The FortiGuard has configured as default to have one hour to keep in cache the URL classifications from web pages that were filtered by some Web Filter profile configured on Firewall and in use in Firewall policy. For Email Filtering, we have 30 minutes. Both values are configurable, and the customization will depend on porpoise. An example of necessity to change is internet links like VSAT, Very Small Aperture Terminal, that some remote locations could demand that the cache time be more than one hour to avoid consuming bandwidth in these limited links. For both, the maximum of cache time is 24 hours.
When the first request is made for a URL, the firewall will only query FortiGuard for the same address after one hour, the default time, or up to 24 hours, which is the longest possible time to maintain the cache. The longer time, as we saw with the VSAT example, can help improve the user experience.
techcyber (fortiguard) # set webfilter-cache-ttl
webfilter-cache-ttl Enter an integer value from <300> to <86400> (default = <3600>).
techcyber (fortiguard) # set antispam-cache-ttl
antispam-cache-ttl Enter an integer value from <300> to <86400> (default = <1800>).
techcyber (fortiguard) #
The command #diagnose webfilter fortiguard statistics list could help the administrator to check the memory consumption of the cache and check other information like a statistic of utilization of FortiGuard Web Filter.
Since the FortiOS release 6.4 the default configuration of FortiGuard to reach the FDN is anycast. At the first moment, the intention was good and welcome to improve reachability of FortiGuard servers, but unfortunately the behavior was not as expected. More often than not it actually creates a problem in reaching the Fortinet servers because the number of servers available is less than desired.
So, to disable anycast and switch back to unicast servers you will need the CLI.
techcyber (fortiguard) # set fortiguard-anycast disable
techcyber (fortiguard) # set protocol udp
techcyber (fortiguard) # set port 8888
techcyber (fortiguard) # set sdns-server-ip 208.91.112.220
techcyber (fortiguard) #
Some ISP's block a no standard traffic over port 53, for that situation the workaround is to use the port 8888. If the ISP block the traffic based on source port, you can put a range.
techcyber # config system global
techcyber (global) # set ip-src-port-range 1031-4999
techcyber (global) # end
The option to set "sdns" can improve the quality of FortiGuard after chose the DNS Server of a specific region that be closer or faster for your ISP. In the link below, you can find the availability of service by region.
https://status.fortimonitor.forticloud.com/fortiguardsdns
If you are having problems with Web Filtering, is necessary check the conectivity of the Firewall to these destinations using the ping and dns resolution:
service.fortiguard.net
update.fortiguard.net
guard.fortinet.net
service.fortiguard.net
If the connectivity to those destinations is ok and still Fortigate Web Filter unable to work correctly, verify if webfilter-force-off is disabled. Enabling this option will turn off the FortiGuard web filtering service. Disabling this option will allow the FortiGuard web filtering service to operate correctly.
techcyber (fortiguard) # set webfilter-force-off disable
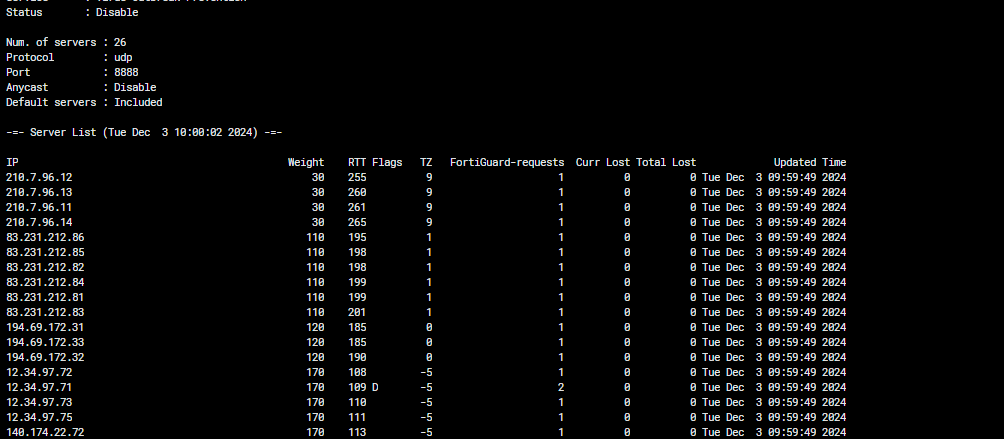
If you are having some instability with Web Filter, you need to check the connection to FDN. So, to verify the quality of connection to FDN, you can use the CLI command #diagnose debug rating to check some information to your troubleshooting. For that command may run, it will be necessary that Web Filter be enabled at least one Firewall policy.
The result of that command, shown above, displays the list of servers for web filtering and antispam queries. For each IP address, the table shows:
• RTT - The round trip delay
• TZ - The server time zone
• Current Lost - The number of recent and consecutive queries without reply
• Total Lost - The historical total number of queries without reply—these values reset when the device restarts.
The FortiGate uses the following method to select the server to send the rating requests to:
• FortiGate initially uses the delta between the server time zone and the FortiGate system time zone, multiplied by 10.
• This is the initial weight of the server. To lower the possibility of using a remote server, the weight is not allowed to drop below the initial weight.
• The weight increases with each packet lost.
• The weight decreases over time if there are no packets lost.
• FortiGate uses the server with the lowest weight as the one for the rating queries. If two or more servers have the same weight, FortiGate uses the server with the lowest round-trip time (RTT).
So, to FortiGuard working as expected, it uses the follow method:
• The FortiGate initially uses the delta between the server time zone and the FortiGate system time zone, multiplied by 10. This is the initial weight of the server. To lower the possibility of using a remote server, the weight is not allowed to drop below the initial weight.
• The weight increases with each packet lost.
• The weight decreases over time if there are no packets lost.
• FortiGate uses the server with the lowest weight as the one for the rating queries. If two or more servers have the same weight, FortiGate uses the server with the lowest round-trip time (RTT).