How to configure VRRP in FortiGate
In today's article we will configure VRRP between two Firewalls that cannot form a cluster and ensure network operation.
FORTINET
10/12/20242 min read
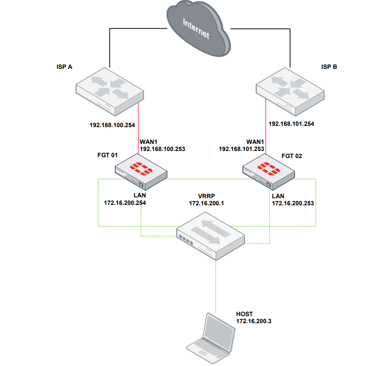
There are topologies in which it is not possible to form a FortiGates cluster. This may be due to the unavailability of layer 2 links for the heatbeat between the firewalls to be connected, hardware differences between the models, or even a way to guarantee the availability of a service or network by different vendors. The protocol that can make these scenarios possible is VRRP (Virtual Router Redundancy Protocol).
It works with two or more routers within a group where, according to priority, one will be active and the others will be on standby. The router, firewall in our topology, defined by priority will use a VIP, Virtual IP address, so that the other routers in the VRRP group will be transparent to hosts on our LAN.
With this feature, single points of failure will be eliminated while increasing the availability and reliability of routing paths in a network.
VRRP can be used per physical interface and VLAN interface. Preferably use version 3 of this protocol, which has some improvements compared to version 2, such as millisecond timers, IPV6 support, among others.
V2 = RFC3768
V3 = RFC5798
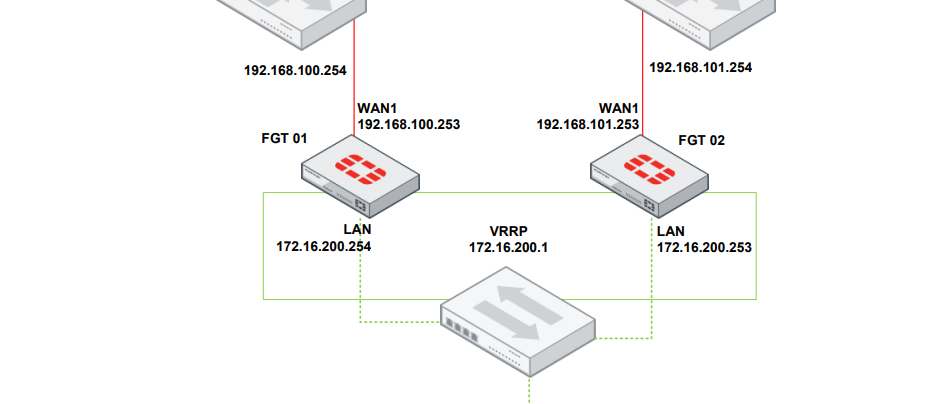
Topology
FortiGate 01 Configuration
FGT01 # config system interface
FGT01 (interface) # edit "VLAN_300"
FGT01 (VLAN_300) # show
config system interface
edit "VLAN_300"
set vdom "root"
set ip 172.16.200.254 255.255.255.0
set allowaccess ping https ssh
set device-identification enable
config vrrp
edit 1
set version 3
set vrgrp 10
set vrip 172.16.200.1
set priority 128
next
end
set role lan
set interface "dmz"
set vlanid 300
nex
end
FGT01 (VLAN_300) #
FortiGate 02 Configuration
FGT02 # config system interface
FGT02 (interface) # edit "VLAN_300"
FGT02 (VLAN_300) # show
config system interface
edit "VLAN_300"
set vdom "root"
set ip 172.16.200.253 255.255.255.0
set allowaccess ping
set device-identification enable
set vrrp-virtual-mac enable
config vrrp
edit 1
set version 3
set vrgrp 10
set vrip 172.16.200.1
set priority 64
next
end
set role lan
set interface "dmz"
set vlanid 300
nex
end
FGT02 (VLAN_300) #
Troubleshooting commands
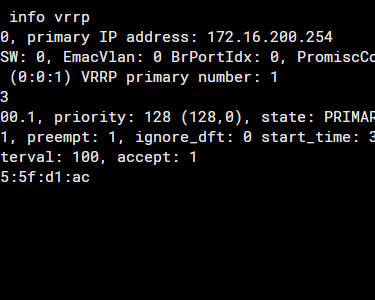
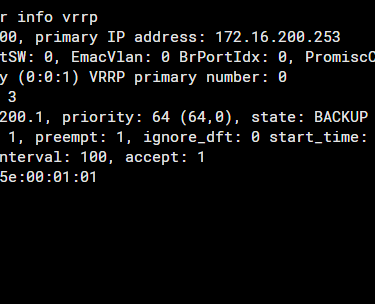
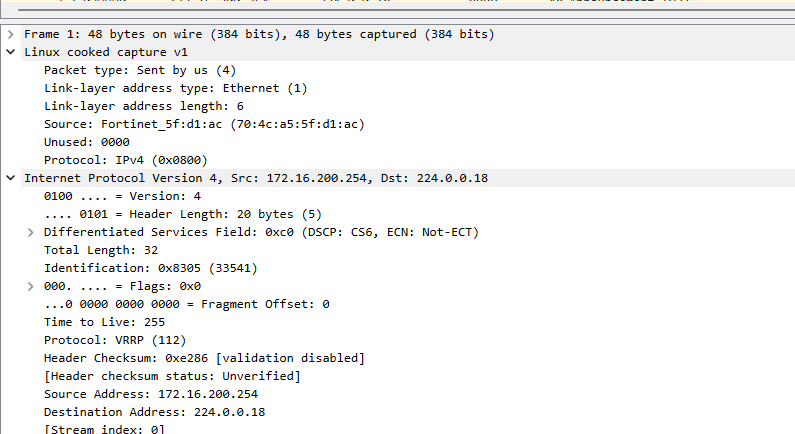
# get router info vrrp
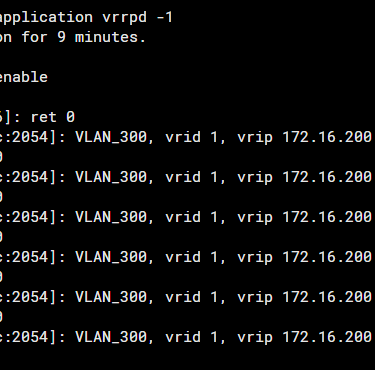
# diagnose deb application vrrpd -1
# diag deb en
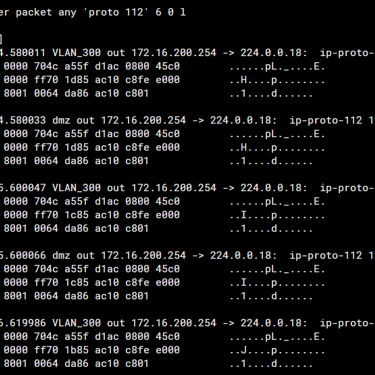
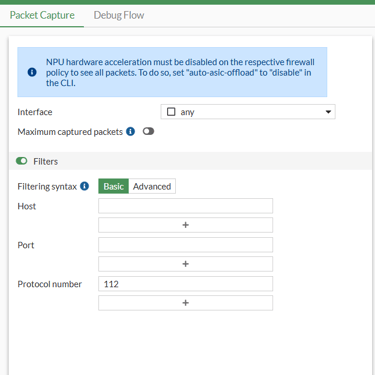
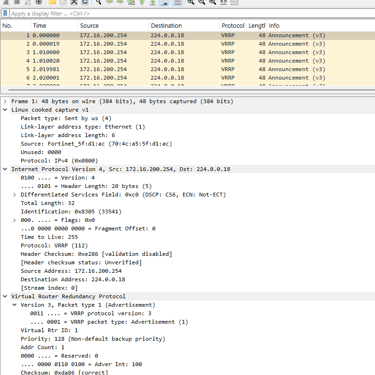
# diag sniffer packet any 'proto 112' 6 0 a
Final Considerations
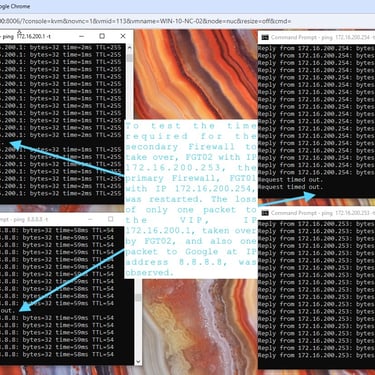
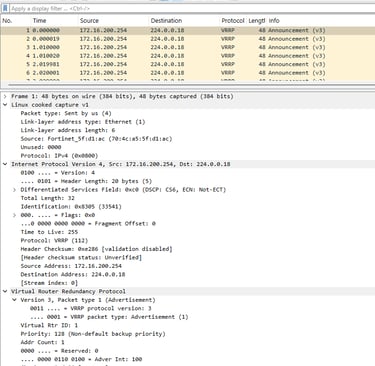
To test the time required for the secondary Firewall to take over, FGT02 with IP 172.16.200.253, the primary Firewall, FGT01 with IP 172.16.200.254, was restarted. Only one packet was lost to the VIP, IP 172.16.200.1, taken over by FGT02, and also one packet to Google at IP address 8.8.8.8. The last image in the gallery shows the test.
It is important to know that if VRRP version 2 is chosen and the priority of the members is the same, the one with the highest IP address value assigned to the interface will be elected as the active member. In our scenario, this would be FGT01.