SSL Inspection - Certificate Inspection vs Deep Inspection
A quick review of how FortiGate certificate inspection methods work. Topic covered in the FCP - FortiGate Administrator exam
SECURITYFORTINET
8/10/20244 min read
I once spoke to a friend who was preparing to obtain the Fortinet FCP certification and who had some questions about the types of inspection and how they worked. Let's try to explain in a simple way, based on some points that I consider important.
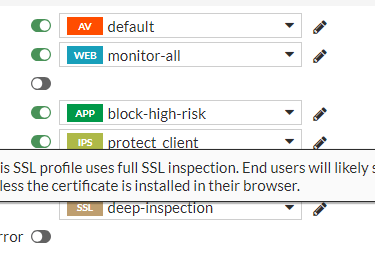
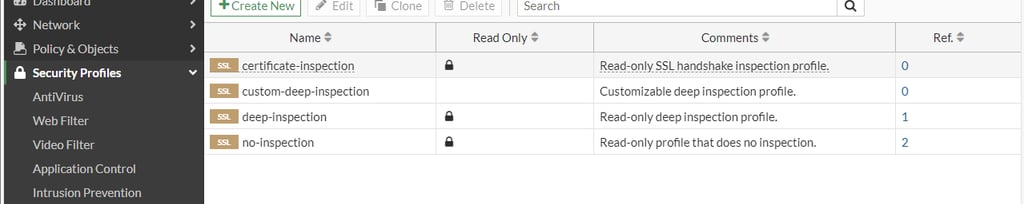
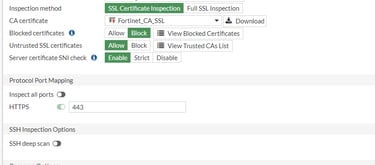
FortiGate provides two types of certificate inspection, the two main ones being certificate inspection and deep inspection. In the image below we see 04 profiles that come by default in the 7.2 release of Forti OS. As the name suggests, the "no-inspection" even with active security profiles, will not perform any analysis or action. Generally used during troubleshooting.
Certificate Inspection
When you use certificate inspection, FortiGate inspects only the headers up to the SSL/TLS layer. This way, web pages such as Instagram and web-based emails can be classified before the user performs authentication.
In this way, Certificate Inspection analyzes the CN field of the certificate, thus not interrupting SSL/TLS communication between the user and the server and without analyzing the encrypted content. It is a very common inspection and considered efficient for allowing or denying web pages where these are the most common actions.
However, if we consider that the https protocol is used by 87.6% of all websites, source: w3techs.com, the certificate inspection method is not ideal for very common applications that make up the security and protection layers such as Anti-Virus, Application Control or IPS. The same goes for Video Filter and WAF.
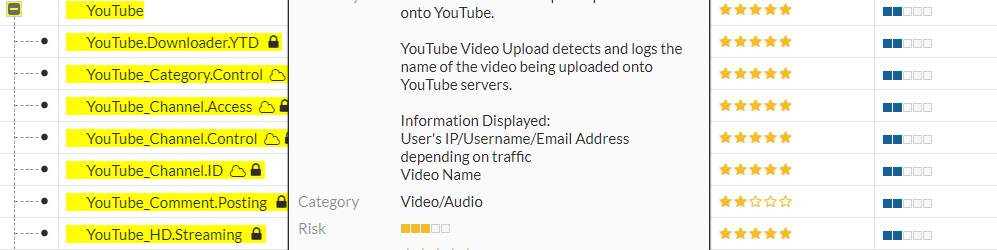
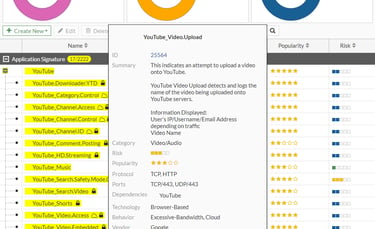
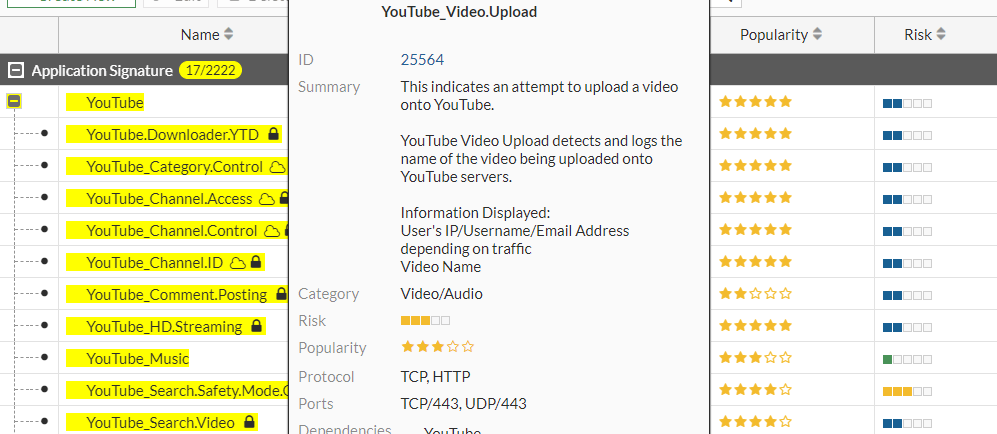
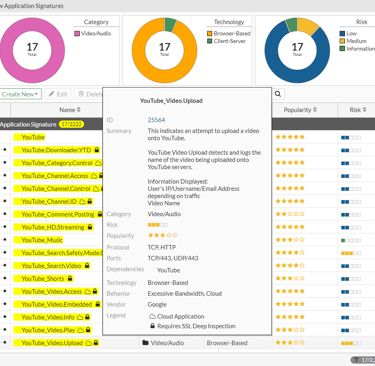
In these applications, the inspection must continue to be in action after the user has authenticated to the application server, considering that the traffic is allowed. The antivirus will need to inspect what is inside the tunnel created between the client and the server, as well as applications and their functionalities such as YouTube with video uploads or Facebook chat and even IPS signature protection for servers, among others, will depend on another type of inspection, deep inspection.
Here is an example of an application that requires deep inspection to have granularity in its use. All the applications with the "lock" icon, require deep inspection, SSL offloading, to work.
Deep Inspection
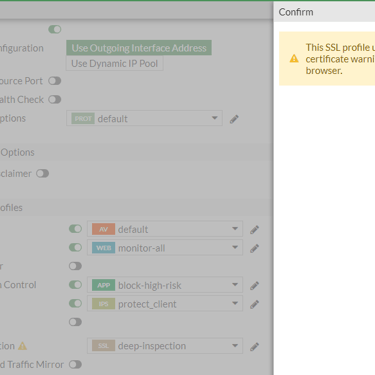
Deep inspection, also known as ssl offloading, decrypts the packets and re-encrypts them using the certificate defined in CA Certificate. This process can generate an error in the user's browser, informing that the certificate is not trusted. This is because the Deep Scan process executes two SSL/TLS sessions, the first between the user's browser and FortiOS using the CA defined in the SSL/SSH Inspection Profile and the second between the requested website and FortiOS, using the website's own certificate. This is known as Man-in-the-Middle, MitM.
For deep inspection to work, users must trust the certificate signed by FortiGate and there must be a certificate chain back to the trusted root CA installed on the user's endpoint. If the root certificate is not installed, the user will receive a certificate warning every time they access a website that is scanned by FortiGate using deep inspection. The administrator must provide the CA certificate to end users if deep inspection is used.
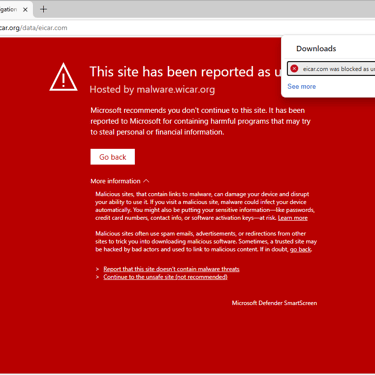
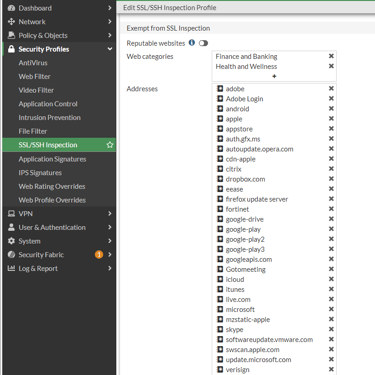
For regulatory reasons, FortiGate does not perform deep inspection on financial and healthcare websites by default. Some websites already analyze and detect if this occurs (MitM) and do not allow the session to be established, alerting the user.
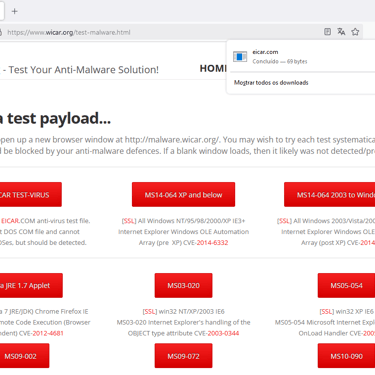
Sites such as eicar.org or wicar.org can offer a simple and quick test to assess the functioning of the Firewall's antivirus. Using the Web Filter, the action will be to allow or deny the page, however, once allowed, as mentioned previously, the inspections must continue and this is where deep inspection comes in.
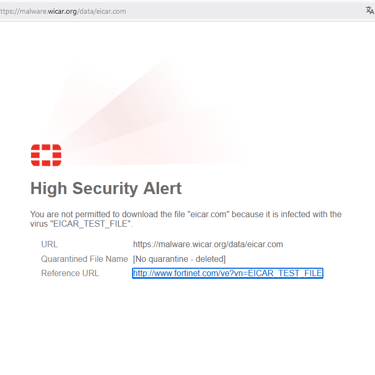
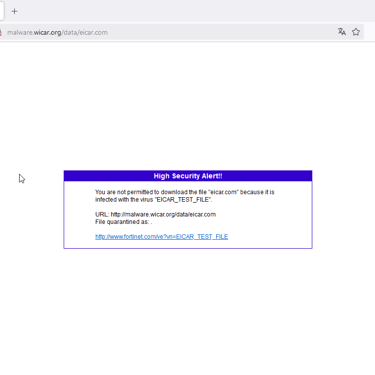
If the inspection is as certificate inspection and the browser does not offer any type of protection and there is no endpoint on the host, the sample file of malicious code, harmless to the system and originating from the mentioned sites, will be downloaded. Now, if the Firewall's antivirus is active in the rule and is in deep inspection, the file will be blocked before being downloaded, fulfilling its role as gateway antivirus.
Recommendations
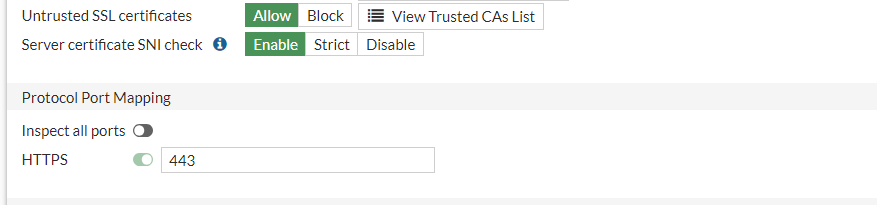
Do not use the default certificate inspection profile as there are changes that can be made to increase security, such as blocking Invalid SSL certificates and Untrusted SSL certificates. The default profile is read-only and such changes are not possible.
For deep inspection, it is preferable to use PKI such as Active Directory and deploy to hosts via group policy.For smaller companies without PKI and/or domains, there are solutions such as Microsoft Endpoint Manager, Intune, which allows device compliance management and can push certificates to devices.
Note
When a firewall policy is in flow-based inspection mode, SSL Certificate Inspection does not validate the certificate. Untrusted SSL certificates and Server Certificate SNI checks are not performed. If these features are required, use proxy-based inspection mode. If you do not want to perform deep scanning for privacy reasons, but want to control access to the website, you can use certificate inspection.
Conclusion
As we can see, certificate inspection is suitable when the inspection type will be restricted to web pages only, using the web filter as a control for guest wifi networks. However, if the administrator wants more layers of protection such as Application Control with more granularity, IPS and AntiVirus, Deep Inspection should be used. Video Filter can only be enabled with Deep Inspection in use.