The risk of LDAP to your network and why to avoid it.
A quick article explaining in a simple way and showing in practice why you should avoid LDAP and other authentication protocols without encryption.
SECURITY
12/31/20241 min read
One of the biggest mistakes that can be made during the implementation of a security project is the use of protocols such as LDAP and RADIUS without encryption. There are still legacy applications that use FTP or even HTTP, which makes these protocols insecure and should not be used.
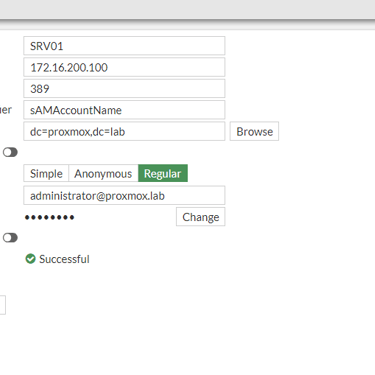
Fortinet's Hardening and Best Practices document, on the first page, already states the reason for using LDAPS and avoiding the use of LDAP. That protocol can be used for both administrative access to the Firewall, internet authentication rules, and even authentication for VPN users, whether IPsec or SSL.
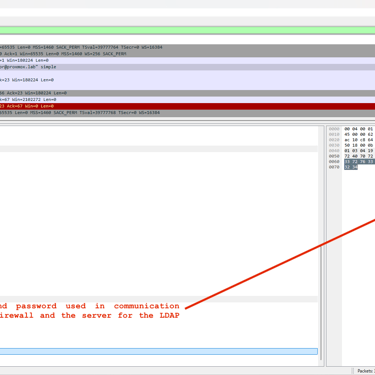
This capture can occur in a variety of ways, from traffic mirroring on a switch port to a compromised host on the same network segment as the server. We will see below how a single capture of LDAP traffic, in addition to the user's password, can compromise the communication password used between the server and the firewall.
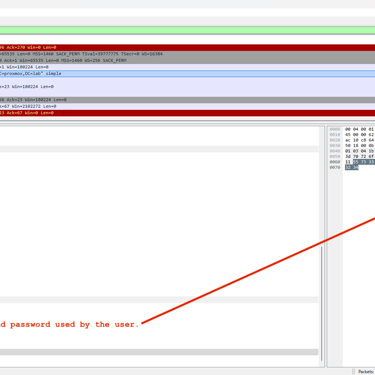
In both images, we can see that both the user's and the administrator's passwords were compromised. Note that even using good password practices such as lowercase and uppercase letters, symbols and numbers will not guarantee compromise since authentication occurs in LDAP. This example also shows the reason why we should use a specific user for this service and the adoption of the principle of least privilege. In the example used, we have the domain administrator being used inappropriately for this service.
Returning to the user's credentials, in environments that use integration with Office 365 in the cloud, without the use of MFA the losses may be even greater.
Although very common and simple to implement, since it will not depend on the server team issuing a certificate to be imported into the Firewall, avoid using LDAP and use LDAPS which uses SSL/TLS in the negotiation.
The same recommendation applies to other protocols that will handle authentication or sensitive traffic.