Threat Feeds - External Connectors in Security Fabric - FortiGate
Some use cases with threat lists in firewall policy and in anti-virus profile
SECURITY
7/18/20242 min read


You can create a lot of integrations on your FortiGate. Some of them could bring a good security improvement beyond the FortiGuard feed.
Knowing that, in the menu Security Fabric we have the option, External Connectors the type Threat Feeds.
Basically, you can use an external and reliable URL list that was fed with malicious IP addresses that was classified in that way, the reason depends on the owner of list, from other vendors or companies. In that lists we can have since IP addresses that did a scan on some services, until address classified such as malicious by private SOC or security consulting companies. In internet, you can find a massive list of threat feeds.
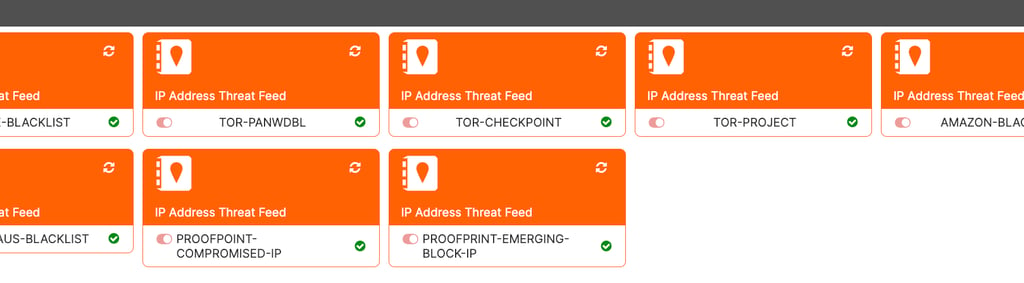
The procedure to create and use it is very simple. Here are some sources of threat feeds that the source are reliable like the Abuse with SSL Blacklist (SSLBL) is a project operated by abuse.ch with the purpose of the project is Collect SSL certificates (SHA1 fingerprints) associated with botnet Command&Control servers (C&Cs) and SSL/TLS client fingerprints (JA3 fingerprints) associated with malware.
So, in the FortiGate CLI:
config system external-resource
edit "ABUSE-BLACKLIST"
set type address
set resource "https://sslbl.abuse.ch/blacklist/sslipblacklist.txt"
next
edit "TOR-PANWDBL"
set type address
set resource "https://raw.githubusercontent.com/jtschichold/panwdbl-actions/tor/exit-nodes.txt"
next
edit "TOR-CHECKPOINT"
set type address
set resource "https://secureupdates.checkpoint.com/IP-list/TOR.txt"
next
edit "TOR-PROJECT"
set type address
set resource "https://check.torproject.org/torbulkexitlist"
next
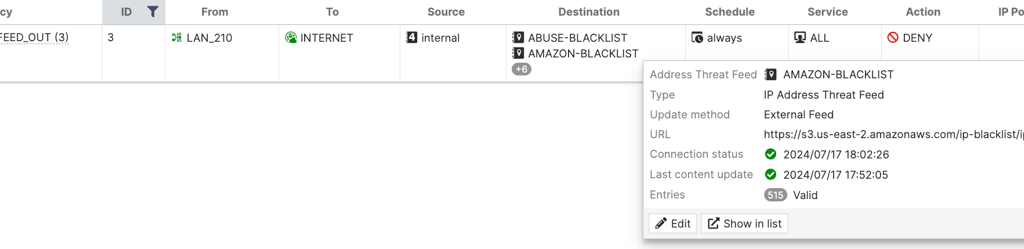
edit "AMAZON-BLACKLIST"
set type address
set resource "https://s3.us-east-2.amazonaws.com/ip-blacklist/ip.txt"
next
edit "SPAMMHAUS-BLACKLIST"
set type address
set resource "http://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt"
next
edit "PROOFPOINT-COMPROMISED-IP"
set type address
set resource "https://rules.emergingthreats.net/blockrules/compromised-ips.txt"
next
edit "PROOFPRINT-EMERGING-BLOCK-IP"
set type address
set resource "https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt"
next
end
After created on GUI:
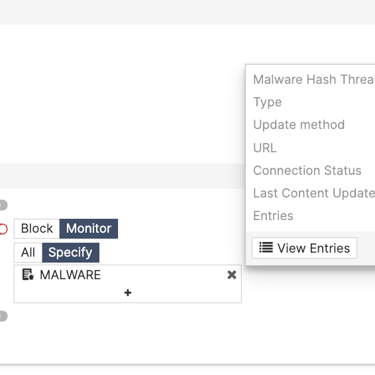
You can create a firewall policy on both directions of traffic to deny the access from addresses IP in that list or a local in policy rule to restrict any of these to try to do some kind of scan on your firewall. After add the list of feed, it will be available on address list.
Many feeds are by subscription and could be more accurate and have more update frequency than those.
It is possible to integrate the FortiGate AV with threat feed for malware with known malicious hashes to improve the protection efficiency.