Using ISDB for security Policy - FortiGate
Some of possible uses for ISDB in security policy at firewall rules.
SECURITY
7/16/20242 min read
The Fortinet ISDB, Internet Service Database, could be much versatile. You can use that in routing policy, static or PBR, traffic shapping policy and others. You can use the Fortinet ISDB to improvement your network security in the both sides of traffic, for outgoing and incoming.
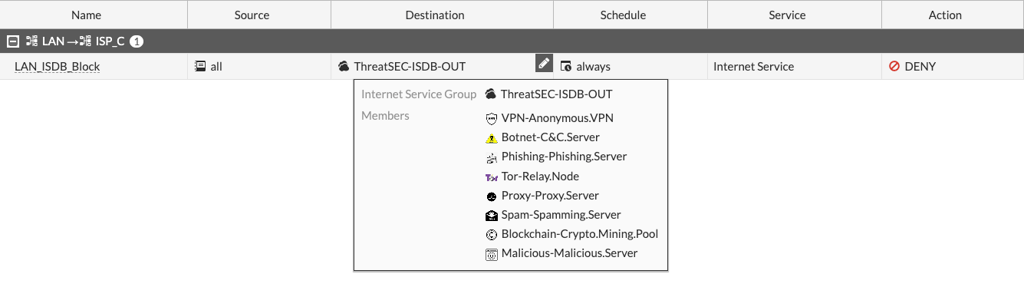
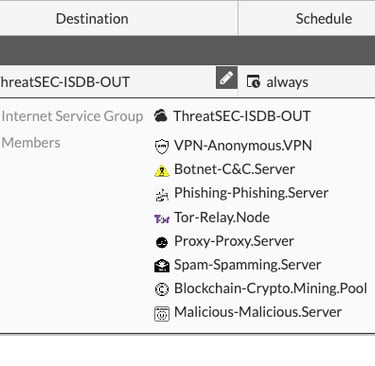
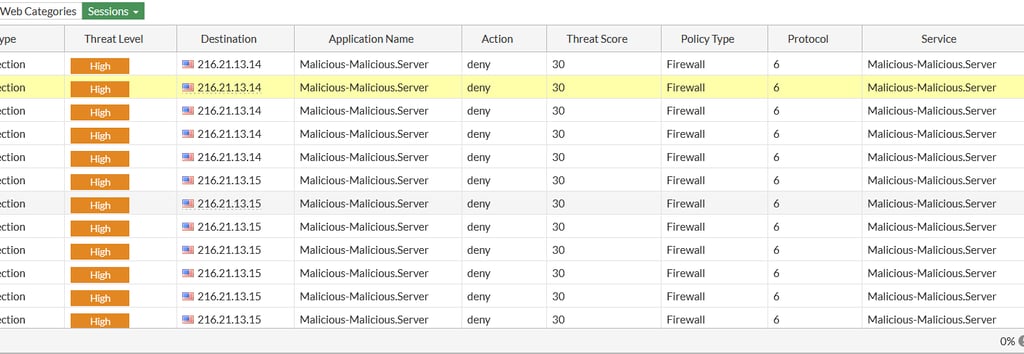
So, we can create a ISDB group with some objects defined and classified by Fortinet as "Malicious" like anonimyzer services to web surfing or botnet servers to command and control. Thar policy should be create above others even when these are using security profiles like applicatin control and web filter. The main point here is, even these profiles are much permissive, that policy can avoid undesired traffic to internet.
Normaly these objects could be used in firewall policy blocking internal traffic to those destinations. The CLI syntax to create the ISDB group to block outgoing traffic will be:
config firewall internet-service-group
edit "ThreatSEC-ISDB-OUT"
set direction destination
set member "VPN-Anonymous.VPN" "Botnet-C&C.Server" "Phishing-Phishing.Server" "Tor-Relay.Node" "Proxy-Proxy.Server" "Spam-Spamming.Server" "Blockchain-Crypto.Mining.Pool" "Malicious-Malicious.Server"
next
end
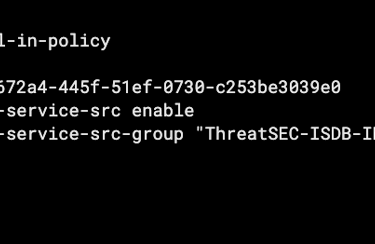
And to block incoming traffic you can create a local in policy rule using ISDB or for blocking in dnat traffic using VIP objects also with ISDB. You can block classified traffic like scanners such as Shodan and similars. The CLI syntax:
config firewall internet-service-group
edit "ThreatSEC-ISDB-IN"
set direction source
set member 'Shodan-Scanner' 'BinaryEdge-Scanner' 'Botnet-C&C.Server' 'Censys-Scanner' 'CriminalIP-Scanner' 'Cyber.Casa-Scanner' 'Internet.Census.Group-Scanner' 'InterneTTL-Scanner' 'LeakIX-Scanner' 'Malicious-Malicious.Server' 'NetScout-Scanner' 'Phishing-Phishing.Server' 'Proxy-Proxy.Server' 'Recyber-Scanner' 'Shadowserver-Scanner' 'Stretchoid-Scanner' 'Tenable-Tenable.io.Cloud.Scanner' 'Tor-Exit.Node' 'Tor-Relay.Node' 'UK.NCSC-Scanner' 'VPN-Anonymous.VPN'
next
end
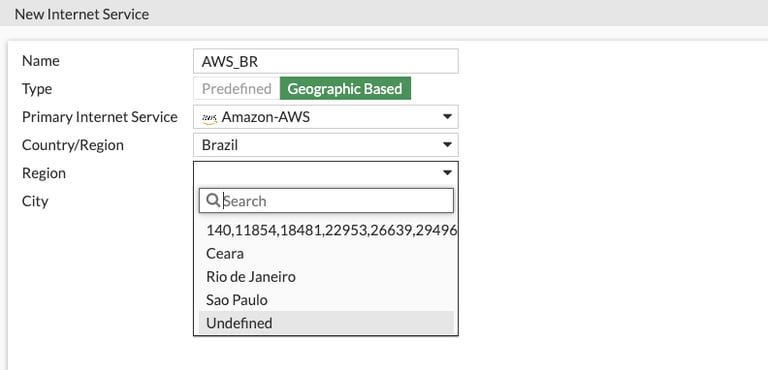
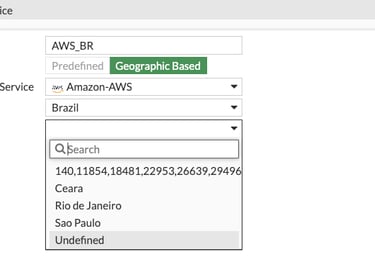
You can create a ISDB objects with regional information. A good example is to limit an API from your AWS region to work.
A two importants considerations are, the usage of ISDB for local in policy is available only in 7.4 Forti OS version and the ISDB entries shown here depends of your firewall local database. That service depends of valid subscription to work as expected.
Keep in mind that security is build in layers so, do what you can towards that goal to the security increasing according to its environment and respective interdependencies.