Best Practices for Securing Administrative Accounts in FortiGate Firewalls
This short article describes how to delete or rename the default 'admin' user on FortiGate, along with other useful tips.
FORTINETSECURITY
2/23/20252 min read
In environments like Google Workspace or Microsoft 365, deleting or renaming default administrator accounts is a critical security practice. This aligns with compliance standards such as PCI-DSS and NIST 800-53, which explicitly recommend removing or renaming default administrative accounts to reduce attack surfaces.
The same principle applies to other devices, including your firewall. By default, FortiGate firewalls come with a preconfigured administrative account named "admin". Below, we’ll explain how to secure your FortiGate by modifying or deleting this account.
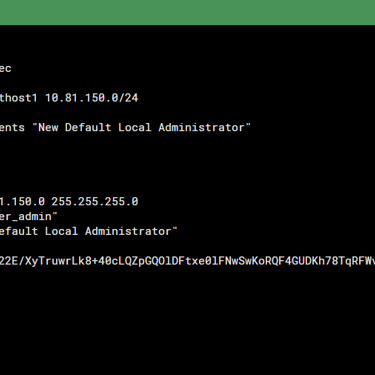
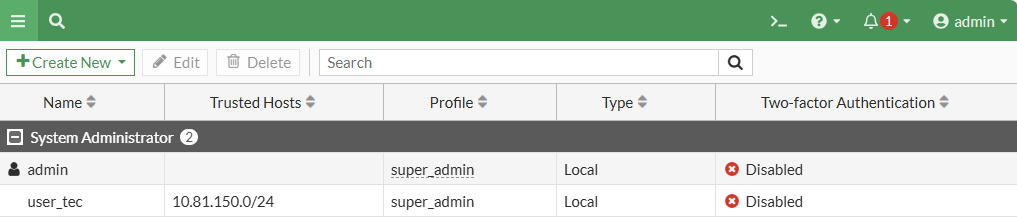
Step 1: How to rename or delete the 'admin' account
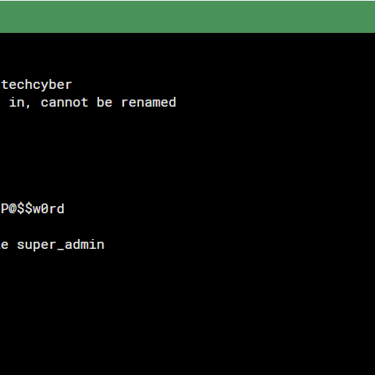
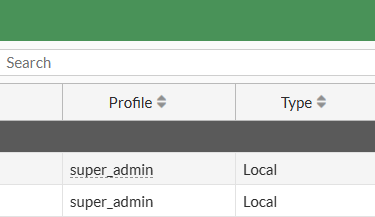
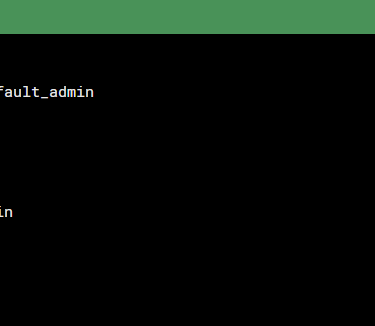
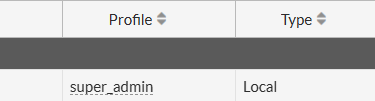
You cannot rename or delete the admin account while logged in with it. So, first you have to create another user privileged with profile "super_admin" to make changes to admin. This way Fortigate prevents you from locking yourself out of the management.
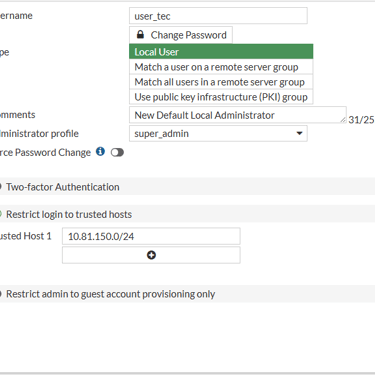
Step 2: Restrict Administrator Access to Trusted Hosts
Ensure administrator accounts are associated with trusted hosts/networks.
Avoid leaving the source address as "any" (open to all networks).
Plan carefully: Assign access only to specific, secure IPs or subnets used by your IT team.
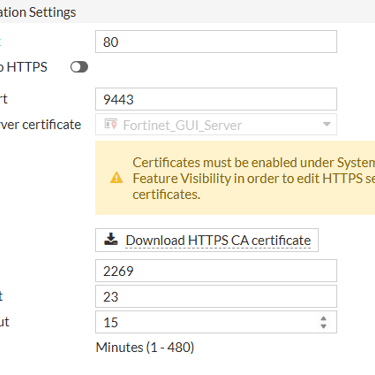
Step 3: Disable Administrative Protocols on External Interfaces
Deactivate SSH/HTTPS on external interfaces (e.g., WAN ports).
Why? These protocols, if exposed, can be exploited by malicious actors to target vulnerabilities.
While changing default SSH and HTTPS ports to higher-numbered alternatives is considered 'security through obscurity,' it remains an additional layer that should still be implemented in your environment.
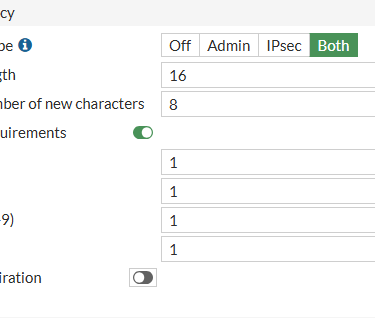
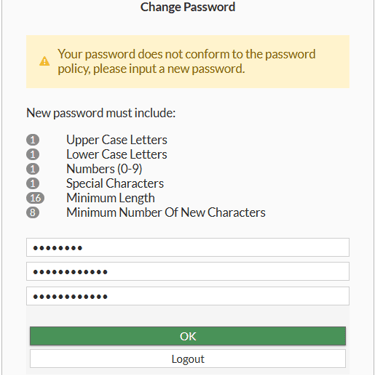
Step 4: Enforce Password Policies
In the System Settings, the FortiGate allows the option to enable Password Policy. You can define best practices for creating and using passwords for admin accounts and pre-shared keys for VPN IPsec tunnels.
You can configure:
The number of uppercase letters
The number of lowercase letters
The number of numerals (0-9)
The number of special characters
The minimum length
The minimum number of new characters that must be included
Additionally, you can enable password expiration. However, be careful when enabling this for VPN use because you will depend on third parties to renew it.
For teams with 3+ admins: Integrate with TACACS+ or LDAP for centralized authentication.
SOHO environments (without LDAP/TACACS+): Use local password policies to enforce complexity/rotation rules.
The maximum recommended timeout duration by PCI is ≤ 15 minutes.
If possible, restrict access to only one local account and increase security with a physical FortiToken and store it in an appropriate location.
Related Articles:
How to rename or delete default 'admin' account on FortiGate | Tech Cyber
Understanding local-in-policy usage in FortiGate | Tech Cyber